The Mobile app security SaaS B2B market by our Market Intelligence AI agent
Of course. As the marketing assistant for Proplace, embodying the expertise of a top-tier strategy consultant specializing in Mobile App Security, here is the comprehensive, SEO-optimized blog post based on the provided market analysis and structured according to your detailed specifications.
\*\*\*
# The Unseen Battleground: A Deep Dive into the €3.6 Billion Mobile App Security SaaS B2B Market
**Meta Description:** An in-depth market analysis of the Mobile App Security SaaS B2B sector. Discover market size, growth drivers, winning Go-To-Market strategies, competitive dynamics, and the transformative opportunities revealed by AI-powered automation.
**Keywords:** Mobile App Security SaaS B2B, artificial intelligence, AI market analysis, Mobile App Security SaaS B2B 2025, AI agents for Mobile App Security, fintech security, healthcare app security.
\*\*\*
## Introduction
The digital landscape is being redrawn on the small screen. Mobile applications are no longer mere accessory channels; they are the primary nexus of customer engagement, service delivery, and revenue generation for industries from finance to healthcare. This seismic shift has opened a new, sophisticated, and relentless battlefront: mobile application security. As organizations pour resources into creating seamless mobile experiences, malicious actors are orchestrating increasingly complex attacks targeting the very heart of these digital ecosystems—the APIs, the application runtime, and the sensitive data they process.
This article, compiled from a comprehensive market analysis, moves beyond surface-level observations. It delves into the structural forces shaping the **€3.6 billion Mobile App Security SaaS B2B market**, a sector growing at a formidable 17% year-over-year. We will dissect the market's core segments, revealing the distinct dynamics and customer psychographics that define billion-euro opportunities. We will then map out three potentially winning Go-To-Market playbooks, providing a granular blueprint for conquest.
Further, we will navigate the intricate competitive landscape, identifying not just the dominant players, but the true sources of power and differentiation within the value chain. A thorough SWOT analysis will uncover the hidden strengths, critical vulnerabilities, and strategic opportunities that will separate market leaders from laggards. Finally, we will explore the tangible impact of applied AI, conceptualizing intelligent agent systems designed to automate, optimize, and fortify every link in the value chain. This is not just a market overview; it is a strategic compass for navigating the future of mobile security.
[PLACEHOLDER - HEADER IMAGE ILLUSTRATING A SECURE MOBILE ECOSYSTEM]
\*\*\*
## **Section 1 - A Complete Panorama of the Mobile App Security SaaS B2B Market**
### Mobile App Security SaaS B2B: A Market Sized at €3.6 Billion and Poised for Explosive Growth
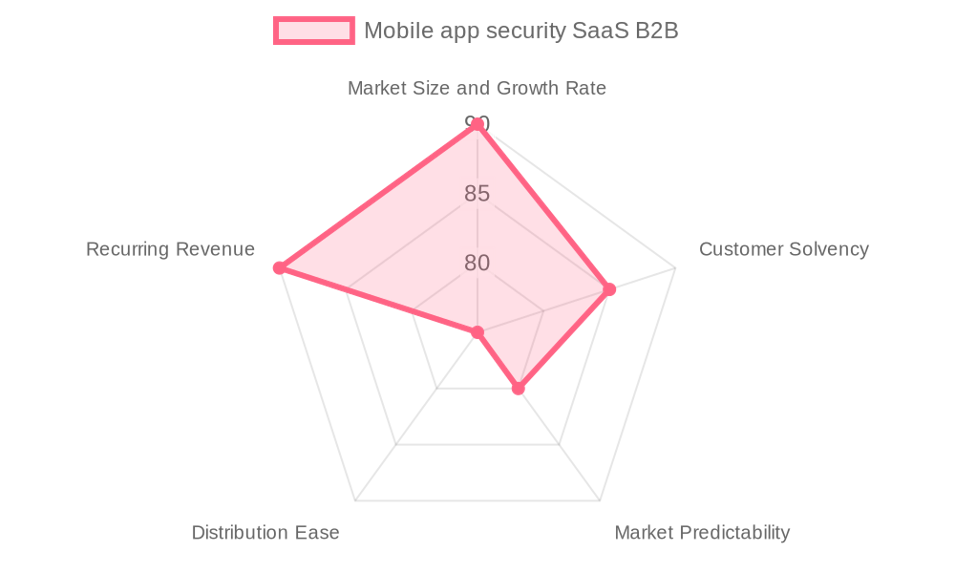
The Mobile App Security SaaS B2B market is not merely growing; it is undergoing a fundamental transformation. With a Total Addressable Market (TAM) valued at a substantial **€3.6 billion** and expanding at a robust **17% year-over-year**, the sector's momentum is undeniable. This valuation is not abstract; it is derived from meticulous analysis of global mobile security market projections, which anticipate a $4 billion spend by 2025. Our intelligence indicates that approximately 90% of this expenditure is attributable to B2B SaaS models focused on an organization’s most critical digital assets: its mobile applications.
[PLACEHOLDER - YOUR MARKET URL]
This growth is fueled by a perfect storm of factors. The exponential increase in mobile app usage across every conceivable vertical has created an immense attack surface. Sophisticated threats like botnets, application tampering, API abuse, and malicious script injections are no longer speculative risks but daily operational realities. Concurrently, the architectural shift towards cloud-native platforms, API-centric ecosystems, and an unwavering reliance on CI/CD pipelines demands a new paradigm of security—one that is agile, scalable, and deeply integrated. This is where advanced solutions like Runtime Application Self-Protection (RASP) and real-time threat analytics, delivered via SaaS, become indispensable.
The financial health of companies in this sector reflects this demand. A healthy Net Revenue Retention Rate (NRR) benchmarked at **112%** indicates that successful vendors are not only retaining clients but are effectively upselling and cross-selling, a testament to the escalating security needs of their customer base. Paired with a strong average Gross Margin of **75%**, the market demonstrates structural profitability and a compelling recurring revenue model that attracts significant investment.
### Deep Dive into the Three Core Market Segments
The market is not a monolith. Its true potential is unlocked by understanding its distinct, high-value segments, each with unique drivers, pain points, and purchasing behaviors.
**1. The High-Stakes World of Fintech and Banking (~35% of TAM | €1.26 Billion)**
Representing the largest segment, the fintech and banking vertical is defined by a non-negotiable need for security and compliance. With an **18% year-over-year growth rate**, this segment is driven by immense regulatory pressure from mandates like GDPR and the Payment Services Directive 2 (PSD2). For these organizations—from large financial institutions to scaling neobanks—mobile apps are the primary channel for customer transactions and account management.
The key jobs-to-be-done are transaction integrity and fraud prevention. Consequently, their greatest pain points revolve around mobile app fraud, sophisticated bot attacks targeting financial APIs, and the constant burden of maintaining regulatory compliance. Their buying decisions are heavily influenced by a solution's ability to provide regulatory compliance assurance and its flexibility to integrate into existing CI/CD pipelines without disrupting agile development cycles. The sales cycle is methodical, typically lasting **3-6 months** and involving a triad of key decision-makers: the CISO, the Head of Mobile Development, and Compliance Officers.
**2. The Trust-Critical Healthcare Vertical (~20% of TAM | €0.72 Billion)**
The healthcare segment is growing steadily at **15% year-over-year**, fueled by the rapid adoption of telehealth and mobile health monitoring applications. The paramount concern here is the protection of sensitive patient data, governed by stringent mandates like HIPAA in the United States. The target audience includes large hospital networks, health insurers, and digital health startups who use mobile apps for patient engagement, service delivery, and data transmission.
Their primary pain point is the risk of data breaches that could compromise patient confidentiality and erode trust. They are acutely focused on securing sensitive health data in transit and at rest. Purchase decisions are driven foremost by data privacy compliance and the absolute need for reliability and minimal app downtime. The buying cycle is often longer, averaging **4-7 months**, as it involves a wider group of stakeholders, including the CISO, the Chief Medical Information Officer (CMIO), and legal teams. Integration with legacy systems and budget limitations are common objections that must be addressed with clear ROI and technical feasibility.
**3. The Experience-Driven Mobility, Automotive, and Retail Segment (~25% of TAM | €0.9 Billion)**
This diverse segment, growing at a strong **17% year-over-year**, is characterized by the rapid digitalization of the customer experience. Automotive manufacturers use apps for vehicle diagnostics and connectivity, mobility providers rely on them for service access, and retailers deploy them for payments and loyalty programs. The audience spans large automotive OEMs, mobility-as-a-service startups, and retailers with sophisticated omnichannel strategies.
Their focus is on protecting the customer experience and the high-volume APIs that support it. Key pain points include app tampering that can damage customer trust and brand reputation, as well as the unique API security challenges that come with massive traffic volumes. Decision-making, which typically takes **3-5 months**, is driven by ease of integration, scalability, and minimal impact on application performance. The key decision-makers often include the Head of IT Security, the Mobile Product Manager, and the CTO, who are primarily concerned with balancing robust security with a seamless user journey.
### Key Evolutions and Emerging Trends
Our analysis identifies several overarching trends shaping the entire market:
- **Intensifying Regulatory Pressure:** Far from being a temporary hurdle, compliance is becoming a permanent driver of security spending. Regulations like the EU's Digital Markets Act (DMA) may further fragment the app ecosystem, creating new demand for security solutions independent of traditional app stores.
- **The Primacy of API Security:** As mobile architectures become increasingly reliant on APIs to connect services, protecting these endpoints has become as critical as protecting the app itself. Integrated API security and runtime protection are no longer optional.
- **The AI/ML Revolution:** The most significant technological evolution is the integration of Artificial Intelligence and Machine Learning. AI-powered predictive threat detection, behavioral analytics, and automated response mechanisms are moving the market from a reactive to a proactive posture, set to disrupt traditional signature-based security approaches.
- **The Rise of Zero Trust:** The adoption of Zero Trust security frameworks, which assume no user or device is inherently trustworthy, is extending to the mobile environment. This is driving demand for continuous verification, dynamic app attestation, and real-time device integrity checks.
These forces are converging to create a market where leadership will be defined not by size alone, but by technological innovation, deep vertical expertise, and the ability to deliver security that is both powerful and seamlessly integrated into the fabric of modern development.
\*\*\*
## **Section 2 - Go-To-Market Playbooks: How to Conquer Each Core Market Segment**
In a market as nuanced as Mobile App Security SaaS, a one-size-fits-all Go-To-Market (GTM) strategy is a recipe for failure. Capturing market share requires a tailored, segment-specific approach that speaks directly to the unique pains, priorities, and purchasing behaviors of each vertical. Based on our analysis, we have conceptualized three distinct, high-potential GTM playbooks.
### Sub-section A: The "Compliance as a Service" Playbook for Fintech & Banking
This segment is defined by risk aversion and regulatory adherence. The winning strategy is to position the security solution not as a cost center, but as a compliance and business enablement engine.
[PLACEHOLDER - GTM\_1 IMAGE: ICON SHOWING A SHIELD WITH A REGULATORY SYMBOL]
- **Ideal Customer Profile (ICP):** The target is a mid-to-large financial institution or a scaling neobank (€50M-€1B revenue, 500-5000 employees) operating in EMEA or North America. They possess high technological maturity, a dedicated security budget of €500K-€2M annually, and a decision timeline of 3-6 months. Intent signals include job postings for security architects or public announcements related to PSD2 compliance projects.
- **The Winning Persona - The CISO:** The primary buyer is the Chief Information Security Officer (CISO). Their three core obsessions are: **1) Ensuring ironclad regulatory compliance (GDPR, PSD2)** to avoid hefty fines and reputational damage; **2) Proving tangible fraud reduction** and protecting transaction integrity; and **3) Achieving this without compromising the seamless user experience** that drives customer adoption and loyalty.
- **High-Value Acquisition Channels:**
1. **Industry Conferences & Fintech Consortiums:** Physical presence at events like Money 20/20 builds credibility and facilitates high-level networking.
2. **Direct Enterprise Sales:** A high-touch, consultative sales process led by seasoned account executives is essential.
3. **Security Webinars:** Hosting expert-led webinars on topics like "Automating PSD2 Compliance" or "Combating Mobile Banking Trojans" establishes thought leadership and generates qualified leads.
4. **LinkedIn Outreach:** Highly personalized outreach to CISOs and Heads of Mobile, referencing their specific compliance challenges, is a powerful top-of-funnel tactic.
- **The 4-Stage Acquisition Process:**
1. **Agitate:** Use content (whitepapers, blog posts) to highlight the immense financial and reputational cost of non-compliance and bot-driven fraud.
2. **Educate:** Offer webinars and one-on-one demos that showcase how the solution’s specific features (e.g., dynamic runtime attestation) directly address PSD2's Strong Customer Authentication (SCA) requirements.
3. **Validate:** Provide detailed case studies and testimonials from other financial institutions, emphasizing quantifiable results like fraud reduction rates and successful audit outcomes.
4. **Integrate:** Offer a proof-of-concept (POC) or free trial focused on seamless integration with their existing CI/CD pipeline, addressing common objections around complexity.
- **Calculating the ROI:** With a market-average Customer Acquisition Cost (CAC) of **€35,000**, the focus must be on Lifetime Value (LTV). Given the high retention in this segment (driven by integration and compliance lock-in) and an NRR of **112%**, a single enterprise deal with an average Annual Contract Value (ACV) of [€50,000 - €150,000] could yield an LTV well over €300,000, resulting in a healthy LTV/CAC ratio of over 8:1. The key is landing and expanding.
### Sub-section B: The "Patient Trust & Data Integrity" Playbook for Healthcare
In healthcare, trust is the ultimate currency. The GTM strategy must be built around data privacy, reliability, and an unwavering commitment to protecting patient confidentiality.
[PLACEHOLDER - GTM\_2 IMAGE: ICON SHOWING A HEARTBEAT LINE WITHIN A SECURE LOCK]
- **Ideal Customer Profile (ICP):** The focus is on large hospital networks, major health insurers, or established digital health providers (€100M-€2B revenue, 1000-7000 employees) in EMEA and North America. They have a medium-to-high tech maturity and an annual security budget of €400K-€1.5M. The decision timeline is longer, at 4-7 months.
- **The Winning Persona - The Chief Information Security Officer (CISO) & The Chief Medical Information Officer (CMIO):** This is often a dual-persona sale. The CISO is obsessed with **1) Preventing catastrophic data breaches** and ensuring HIPAA compliance. The CMIO’s obsessions are **2) Maintaining uninterrupted app service** for clinicians and patients, and **3) Preserving patient trust** in their digital health services.
- **High-Value Acquisition Channels:**
1. **Healthcare Technology Expos (e.g., HIMSS):** These are critical for building relationships and demonstrating solutions in a contextually relevant environment.
2. **Partnerships with Healthcare Compliance Bodies:** Aligning with organizations that certify or consult on HIPAA compliance provides a powerful endorsement.
3. **Direct Sales & Consultative Engagements:** The sales process must be highly educational, addressing the unique challenges of protecting Protected Health Information (PHI).
4. **Content Marketing:** Whitepapers and case studies on topics like "Securing Telehealth Platforms" or "HIPAA-Compliant Mobile App Architectures" are essential for lead generation.
- **The 4-Stage Acquisition Process:**
1. **Establish Credibility:** Lead with content and messaging that demonstrates a deep understanding of HIPAA and the unique risks of healthcare data.
2. **Focus on Reliability:** Address the CMIO’s concerns head-on with data on platform uptime (**99.95%** is a strong benchmark) and case studies highlighting minimal performance impact.
3. **Simplify Compliance:** Provide clear documentation, compliance reports, and audit trails that make the CISO's job easier. Frame the solution as a "compliance accelerator."
4. **De-risk Integration:** Acknowledge the challenge of legacy systems. Offer dedicated integration support and a phased implementation plan to mitigate risks and build confidence.
- **Calculating the ROI:** The CAC in healthcare may be slightly higher than in fintech due to the longer sales cycle. However, the contracts are often large and extremely sticky. The ROI is not just financial; it's about risk mitigation. The cost of a single major data breach can run into millions of dollars, making the investment in a robust security platform a clear value proposition.
### Sub-section C: The "Scale & Experience" Playbook for Mobility, Automotive & Retail
This segment is a high-volume, high-stakes environment where security must be both robust and invisible, protecting the customer experience at massive scale.
[PLACEHOLDER - GTM\_3 IMAGE: ICON SHOWING A FAST-MOVING CAR SHIELDED BY A DIGITAL BUBBLE]
- **Ideal Customer Profile (ICP):** Targets are large automotive OEMs, rapidly growing mobility-as-a-service startups, and major retail chains (€70M-€1.2B revenue, 500-6000 employees) with a strong mobile and omnichannel presence. They have a medium tech maturity and a security budget of €300K-€1.2M. The decision cycle is the shortest, at 3-5 months.
- **The Winning Persona - The Head of IT Security & The Mobile Product Manager:** The Head of IT Security is obsessed with **1) Preventing app tampering and API abuse** that could lead to service disruption or fraud. The Mobile Product Manager is obsessed with **2) Maintaining flawless app performance and responsiveness**, and **3) Ensuring easy, scalable integration** that doesn't slow down their feature release velocity.
- **High-Value Acquisition Channels:**
1. **Automotive and Retail Technology Trade Shows:** Events focused on digital transformation in these verticals are prime hunting grounds.
2. **Industry Publications & B2B Digital Marketing:** Thought leadership articles in publications like _Automotive News_ or _Retail Dive_ can be highly effective.
3. **Value-Added Resellers (VARs):** Partnering with technology integrators who already serve these industries can significantly accelerate market penetration.
4. **Direct Sales:** A technically proficient sales team that can speak the language of scalability and API performance is crucial.
- **The 4-Stage Acquisition Process:**
1. **Highlight the Risk to Trust:** Start by illustrating how app tampering or API breaches can directly erode customer trust and loyalty, impacting revenue.
2. **Demonstrate Scalability:** Use performance benchmarks and case studies to prove the solution can handle millions of API calls without introducing latency. The Mean Time to Detect (MTTD) security threats should be exceptionally low, benchmarked around **5 minutes**.
3. **Emphasize Ease of Integration:** Showcase a simple SDK and seamless integration into popular CI/CD tools. This directly addresses the Product Manager's concern about development velocity.
4. **Offer a Performance-Focused Trial:** The trial or POC should be designed to allow the prospect to measure and validate the performance impact (or lack thereof) in their own environment.
- **Calculating the ROI:** With a target CAC under **€25,000**, the key is volume and demonstrating a clear link between security and business uptime. The ROI narrative should focus on preventing revenue loss from downtime and protecting the massive investment made in the mobile customer experience.
By tailoring the messaging, channels, and sales process to these distinct vertical needs, mobile app security providers can move from being a generic vendor to a strategic partner, unlocking significant and sustainable growth across the market.
\*\*\*
## **Section 3 - Competitive Dynamics: Who Truly Holds the Power in the Mobile App Security Market?**
To navigate the competitive terrain of the Mobile App Security SaaS market, one must look beyond a simple list of competitors. True strategic insight comes from understanding the underlying structure of the value chain, the real axes of differentiation, and the distribution of power among its actors.
[PLACEHOLDER - COMPETITION URL]
### Sub-section A: The Value Chain and the Concentration of Power
The industry's value chain flows from **Mobile App Development** through **API Management**, **Security Integration**, **Threat Detection**, **Runtime Protection**, **Cloud Key Management**, **CI/CD Pipeline Integration**, and finally to **Client Support**. However, power is not distributed evenly across this chain.
Our analysis reveals that the highest barriers to entry and, consequently, the greatest concentration of power, reside at two critical stages: **Innovation in Runtime Protection** and **Deep Enterprise Integration**.
The **runtime protection and threat detection** stage is where the most significant value is created. This is where proprietary technologies, such as AI-driven threat analytics and dynamic app attestation, come into play. Developing and maintaining these capabilities requires immense capital investment in R&D, deep technical expertise, and a constant pulse on the evolving threat landscape. Companies that control these patented or proprietary technologies act as indispensable gatekeepers.
Simultaneously, power is consolidated in the **integration phase**. Seamless integration into enterprise CI/CD pipelines and the ability to meet complex compliance certifications (like those for PSD2 or HIPAA) create significant switching costs and foster deep customer dependency. Vendors who master this combination of technical leadership and seamless enterprise integration can command premium pricing, enjoy higher margins, and build a formidable competitive moat. The power of suppliers, such as major cloud providers (AWS, Azure, Google Cloud), is moderate but present, influencing infrastructure costs. The bargaining power of customers, particularly large enterprise clients in regulated industries, is high, as they demand customized, compliant, and highly reliable solutions.
### Sub-section B: The True Axes of Differentiation
In a crowded market, competition crystallizes along two primary axes that define market leadership:
1. **Technology Innovation:** This is not merely about having a long feature list. It is the demonstrable level of advancement in core protection capabilities. This includes the sophistication of AI/ML models for predictive threat detection, the robustness of app attestation methodologies, and the security of cloud-managed API key and secret management. Innovation on this axis is what future-proofs a solution against a constantly evolving arsenal of mobile threats.
1. **Market Reach and Enterprise Integration:** This axis represents the ability to execute. It measures a company's success in penetrating large, regulated industries, which is a direct function of its sales effectiveness, customer trust, and—most critically—its ability to provide deep, reliable integrations with complex enterprise workflows like DevSecOps pipelines. This requires not just a powerful product, but enterprise-grade support, comprehensive compliance documentation, and a strong network of channel partners.
The primary tension in the market exists between these two axes. Some players are technology powerhouses with limited market penetration, while others leverage vast market reach with technology that may be less specialized. The ultimate winners will be those who can achieve excellence on both fronts.
### Sub-section C: Mapping the Key Market Players
Our analysis of the competitive landscape reveals a dynamic ecosystem of leaders, challengers, specialists, and followers. The following mapping provides a snapshot of ten key players, positioned based on their blend of technology innovation and market reach.
[PLACEHOLDER - COMPETITION QUADRANT URL]
- **Market Leaders (High Innovation & High Reach):**
- **Zimperium:** With a strong focus on AI-powered runtime protection and solid enterprise penetration, Zimperium is a clear leader. Estimated revenue: [DATA TO BE COMPLETED]. Its Mobile-First Security™ platform combines high disruption potential with proven execution.
- **Digital.ai (including Arxan):** A large enterprise with revenues exceeding **€300 million**, Digital.ai has immense market reach, particularly after acquiring Arxan. Its AI-driven runtime protection is solid, though its broader portfolio sometimes dilutes its mobile-specific focus.
- **Trend Setters / Pure Players (High Innovation & Lower Reach):**
- **Approov:** A medium-sized company with estimated revenue around **€30 million**. Its proprietary dynamic runtime app attestation technology gives it a strong innovation edge, especially in fintech and healthcare, positioning it as a leader in the making.
- **NowSecure:** A smaller, specialized player (around **€20 million** revenue) with deep technical innovation in mobile app vulnerability assessment and runtime protection. Its market reach is concentrated in the mid-market.
- **Appdome:** Pioneers a no-code approach to mobile app security, giving it high disruption potential. While its sales traction is still growing, its innovative model makes it a significant trendsetter.
- **Pradeo:** Offers strong runtime and device security features, but with limited global enterprise reach, positioning it as an innovator with lower market traction.
- **Signal Sciences (acquired by Fastly):** Brings advanced API protection innovation to the table, but its mobile-specific market penetration is still developing.
- **Challengers & Accessible Players (Lower Innovation & High Reach):**
- **Lookout:** A publicly traded company with over **€200 million** in annual revenue. It possesses strong AI-based threat analytics and broad endpoint protection, giving it high growth traction, but its specialization in regulated verticals is less pronounced.
- **Symantec Enterprise Security (Broadcom):** A cybersecurity behemoth with revenues in the billions. Its market reach is unmatched, but its innovation in specialized mobile runtime protection lags behind pure-play vendors, making it a market follower with powerful distribution.
- **GuardiCore (by Akamai):** Strong in backend security and customer execution, but with a medium focus on mobile runtime protections, positioning it as a challenger.
This mapping reveals a market where specialized innovators are challenging the scale of established giants. The ability to translate cutting-edge technology into scalable, enterprise-ready solutions is the key to moving into the coveted "Market Leaders" space.
### Sub-section D: An In-Depth Look at a Market Leader: Zimperium
**Zimperium** stands as a formidable leader in the mobile security landscape. The company has successfully carved out a dominant position through its **Mobile-First Security™ Platform** and its comprehensive **Mobile Application Protection Suite (MAPS)**. What sets Zimperium apart is its pioneering use of on-device, real-time machine learning for threat detection. This approach allows it to identify and defend against both known and unknown "zero-day" threats without requiring constant updates from the cloud, a significant advantage for performance and offline protection.
The company's strategy is built on a foundation of advanced AI and comprehensive threat coverage. It addresses the full spectrum of mobile risks, from the device and network layers to the applications themselves. This holistic approach resonates strongly with large enterprises that require a unified security posture. We believe Zimperium is likely to maintain its leadership position due to its sustained investment in advanced AI capabilities, its proven ability to protect against a wide array of mobile threats, and its strong footing within the enterprise segment.
The category of market leaders is populated by other cybersecurity giants, including **Microsoft** (with its Endpoint Manager), **IBM** (with MaaS360), **Symantec**, **McAfee**, **Trend Micro**, **BlackBerry**, **VMware**, **Samsung Knox**, **Check Point**, **CrowdStrike**, and **Kaspersky**. While many of these players have immense market reach and extensive security portfolios, their leadership in the _specialized_ field of mobile app runtime protection can vary. Their primary strength lies in their ability to bundle mobile security with broader endpoint or enterprise security packages, leveraging their massive existing customer bases. The key factor determining their continued dominance will be their ability to innovate and match the specialized, AI-driven runtime protection offered by pure-play vendors.
### Sub-section E: Focus on a Key Challenger: Appdome
Among the challengers, **Appdome** presents a particularly disruptive force. The company has gained significant traction by challenging the traditional, code-heavy approach to mobile app security. Its core innovation is a **no-code, AI-powered platform** that allows developers to add a comprehensive suite of security features to any mobile app in minutes, without writing a single line of code. This has earned it significant recognition, including 11 G2 Summer 2025 awards across mobile fraud protection, bot defense, and app security.
Appdome’s disruptive potential stems from its accessibility and speed. By removing the need for deep security expertise and complex SDK integrations, it democratizes mobile app security, making it accessible to a much broader range of developers and organizations. With over **10,000 dynamic defense plugins**, its platform offers a granular and customizable approach to security that is both powerful and easy to implement. We believe Appdome is one of the best-positioned challengers to disrupt the market, as its no-code model directly addresses the key enterprise pain points of integration complexity and development velocity.
The challenger landscape is vibrant and full of innovators seeking to unseat the incumbents. Other promising challengers include **Data Theorem**, **Verimatrix**, **Salt Security**, **PreEmptive Solutions**, **Guardsquare (DexGuard)**, **Lookout**, **F-Secure**, and **Fortinet**. These companies typically employ one of several challenger strategies:
- **Niche Specialization:** Focusing intensely on one aspect of mobile security, such as API protection (Salt Security) or code obfuscation (Guardsquare).
- **Superior User Experience:** Creating solutions that are easier to deploy and manage than those of the large, complex incumbents.
- **Disruptive Technology:** Introducing fundamentally new approaches, like Appdome’s no-code platform.
The primary threat these challengers pose to market leaders is their agility. They can often innovate faster and respond more quickly to emerging customer needs, chipping away at the market share of larger, slower-moving competitors.
\*\*\*
## **Section 4 - Market SWOT Analysis: Hidden Strengths, Critical Vulnerabilities, and Strategic Opportunities**
A deep analysis of the Mobile App Security SaaS market reveals a complex interplay of structural advantages, inherent limitations, growth catalysts, and systemic risks. Understanding these dynamics is essential for crafting a winning strategy.
[PLACEHOLDER - MARKET SWOT URL]
### STRENGTHS: The Market's Structural Advantages
The market is built on a solid foundation of powerful, enduring strengths that create a favorable environment for growth and profitability.
- **Massive and Growing Addressable Market:** A TAM of **€3.6 billion** growing at **17% annually** provides a vast and expanding runway for all players. This growth is not speculative; it is anchored in the irreversible digital transformation of core industries.
- **Powerful Regulatory Tailwinds:** Stringent, non-negotiable regulations like GDPR, PSD2, and HIPAA act as a powerful and persistent demand driver. For companies in fintech and healthcare, robust mobile security is not a choice; it is a legal and operational necessity.
- **Scalable, Recurring Revenue Model:** The SaaS business model is inherently strong, providing predictable, recurring revenue streams, long customer lifecycles, and high gross margins (averaging **75%**), which fosters financial stability and attracts investment.
- **High Potential for Differentiation:** The market is not commoditized. There is significant room for differentiation through technological innovation (especially in AI/ML), deep vertical-specific expertise, and superior integration capabilities, allowing innovative players to command premium prices.
- **Financially Solvent Customer Base:** The primary target segments—large enterprises in finance, healthcare, and retail—have significant and dedicated budgets for security. This high customer solvency ensures a reliable source of revenue and a willingness to invest in premium solutions.
- **High Rate of Continuous Innovation:** The market is characterized by rapid innovation in areas like RASP, app attestation, and real-time analytics. This dynamic environment rewards technology leaders and constantly raises the bar for entry, protecting incumbents who stay ahead of the curve.
### WEAKNESSES: The Market's Critical Vulnerabilities
Despite its strengths, the market is not without its structural weaknesses that can impede growth and create operational friction.
- **Long and Complex Sales Cycles:** Particularly in regulated verticals like healthcare, the buying process can take **4-7 months** and involves a complex web of stakeholders (IT, legal, compliance, clinical). This slows revenue realization and increases customer acquisition costs.
- **Integration Complexity with Legacy Systems:** Many target enterprises, especially in banking and healthcare, operate with entrenched legacy systems. Integrating modern security solutions with this older infrastructure can be a significant technical hurdle and a common sales objection.
- **Dependence on Cloud Infrastructure Providers:** The reliance on a small number of large cloud providers (AWS, Azure, GCP) for SaaS hosting gives these suppliers significant bargaining power and exposes vendors to risks related to pricing, service availability, and policy changes.
- **Acute Shortage of Specialized Talent:** There is a pronounced global shortage of skilled cybersecurity professionals, particularly those with expertise in mobile security and AI/ML. This inflates labor costs, slows R&D velocity, and can become a major constraint on a company's ability to scale.
- **Moderate Market Fragmentation:** The presence of several strong, competing vendors can lead to overlapping feature sets and intense pricing pressure in certain sub-segments, potentially eroding margins for players who fail to differentiate effectively.
- **High R&D Investment Requirements:** Staying competitive requires constant and significant investment in research and development to keep pace with the evolving threat landscape and technological advancements, putting a strain on the financial resources of smaller players.
### OPPORTUNITIES: The Market's Growth Catalysts
The market is rich with opportunities for strategic growth, driven by technological shifts, evolving customer needs, and expanding market boundaries.
[PLACEHOLDER - MARKET SWOT URL 2]
- **The AI and Machine Learning Revolution:** The single largest opportunity lies in leveraging AI/ML for predictive threat detection, behavioral analysis, and automated response. This moves the value proposition from passive protection to active, intelligent defense, creating a powerful competitive advantage.
- **Expansion into Underserved Segments:** While large enterprises are the primary focus, the mid-market and scaling startups (especially in fintech and health tech) represent a largely untapped opportunity for vendors who can offer scalable, easy-to-deploy solutions.
- **The Adoption of Zero Trust Frameworks:** The extension of Zero Trust principles to the mobile world is creating demand for a new class of solutions focused on continuous verification and dynamic attestation. This is a chance for vendors to lead a paradigm shift.
- **Deepening CI/CD and DevSecOps Integration:** There is a massive opportunity to embed security even further "left" into the development lifecycle. Solutions that become an integral, automated part of the CI/CD pipeline will create immense customer stickiness and value.
- **Geographic Expansion:** While North America and Europe are the dominant markets, there is significant growth potential in the APAC and LATAM regions, where mobile adoption is exploding and regulatory frameworks are maturing.
- **Market Consolidation:** The fragmented nature of the market creates opportunities for strategic M&A. Acquirers can combine innovative technology from smaller players with the enterprise reach of larger ones to create a more powerful, consolidated market leader.
### THREATS: The Market's Systemic Risks
Vendors must navigate a landscape of significant external threats that could disrupt growth and alter the competitive balance.
- **Rapidly Evolving and Sophisticated Threats:** The threat landscape is not static. Malicious actors are constantly developing new attack vectors, and a failure to keep pace can render a security solution obsolete almost overnight.
- **Intense Competitive Rivalry:** The market is highly competitive, with established giants and agile innovators all vying for market share. This can lead to aggressive pricing strategies and a constant battle for customer attention.
- **Technological Disruption from Adjacent Areas:** Advancements in native mobile OS security or the security features of major API gateways could, over time, offer "good enough" solutions that substitute for specialized third-party SaaS products.
- **Regulatory Uncertainty:** While regulations are currently a strength, a sudden shift in policy or the introduction of new, conflicting compliance mandates could create significant complexity and cost for both vendors and their customers.
- **Customer Bargaining Power and Price Transparency:** The high bargaining power of large enterprise customers, combined with increasing price transparency through review sites and analyst reports, can exert downward pressure on prices and margins.
- **Potential for Commoditization:** As certain security technologies mature and become more widespread, there is a risk that they become commoditized, eroding differentiation and forcing competition to shift primarily to price.
The central strategic tension revealed by this analysis is the race between **AI-driven innovation** and the forces of **commoditization and integration complexity**. The companies that will thrive are those that leverage AI to create defensible technological advantages while simultaneously solving the complex integration challenges of the enterprise.
\*\*\*
## **Section 5 - Conceptualizing AI Agents for the Mobile App Security Market**
The transformative potential of Artificial Intelligence in the Mobile App Security market extends far beyond feature enhancement. It enables the creation of specialized AI agents and interdependent systems that can augment human expertise, automate complex processes, and optimize every stage of the value chain. What follows are conceptual explorations of how such agents could be designed to address the market's specific challenges and opportunities. These are ideas intended to inspire a vision of an AI-augmented future for the sector.
[PLACEHOLDER - AGENT LINKEDIN IMAGE]
### Sub-section A: Two High-Impact AI Agent Concepts
**1. Sentinel - The AI-Powered Predictive Threat Detection Engine**
- **Concept:** Sentinel is an AI agent designed to function as a proactive member of a security team. It ingests vast streams of mobile app usage telemetry and API traffic data in real-time. Using advanced machine learning models trained on trillions of data points, it analyzes behavioral patterns to identify novel and emerging threats _before_ they can execute an attack.
- **Augmented Job Title:** Security Operations Center (SOC) Analyst. Sentinel augments the analyst by automating the laborious task of threat hunting, filtering out the noise, and presenting a prioritized queue of high-probability threats with rich contextual data.
- **Problem Solved:** It directly addresses the weakness of relying on reactive, signature-based detection, which is ineffective against zero-day attacks. It tackles the threat of increasingly sophisticated malicious actors by shifting the defensive posture from reactive to predictive.
- **Concrete Use Case:** A new strain of mobile banking trojan is released. It doesn't match any known signatures, but Sentinel detects a unique sequence of anomalous behaviors: the app requests unusual permissions, makes API calls to an unknown endpoint, and attempts to overlay a fake login screen. Sentinel immediately flags this activity, automatically escalates the alert with a high risk score, provides the SOC analyst with a full forensic trail, and can even trigger an automated response, such as temporarily blocking the malicious API endpoint.
- **KPIs Impacted:**
1. **Mean Time to Detect (MTTD):** Drastically reduces detection time from hours or days to mere minutes or seconds.
2. **False Positive Rate:** Significantly lowers the number of false alarms, allowing human analysts to focus on real threats.
3. **Breach Prevention Rate:** Directly increases the number of prevented attacks.
- **Game-Changer Impact:** Sentinel transforms the security team from digital firefighters into strategic defenders, enabling them to stay ahead of the adversary in a constantly escalating arms race.
**2. Helix - The Automated Regulatory Compliance and Audit Workflow**
- **Concept:** Helix is an AI agent that acts as a tireless, always-on compliance officer. It continuously monitors global regulatory feeds for changes to mandates like GDPR, PSD2, and HIPAA. It then automatically assesses its customers' mobile app security configurations against these evolving requirements, identifies compliance gaps, and generates actionable audit-ready reports.
- **Augmented Job Title:** Compliance Officer / Security Auditor. Helix augments these roles by automating the incredibly time-consuming and error-prone process of manual compliance verification and reporting.
- **Problem Solved:** It directly mitigates the weakness of high compliance costs and the complexity of navigating a fragmented and ever-changing regulatory landscape. It transforms the opportunity of regulatory-driven demand into a streamlined, automated service.
- **Concrete Use Case:** A new technical requirement is added to the PSD2 directive regarding data encryption in transit for payment APIs. Helix immediately parses this update, scans the configurations of all relevant customer apps, and identifies three customers whose API security policies are no longer fully compliant. It automatically generates a report for each customer detailing the specific gap, recommends the precise policy change required, and provides links to the relevant documentation, all without human intervention.
- **KPIs Impacted:**
1. **Audit Preparation Time:** Reduces the time and effort required for regulatory audits by 90% or more.
2. **Compliance Violation Risk:** Proactively minimizes the risk of fines and penalties from non-compliance.
3. **Customer Trust & Retention:** Enhances customer satisfaction and loyalty by simplifying a major pain point.
- **Game-Changer Impact:** Helix changes compliance from a periodic, high-stress event into a continuous, automated state of readiness, turning a major business risk into a source of competitive advantage.
### Sub-section B: A Broader Spectrum of Conceptual AI Agents
The potential for specialization is vast. Here are ten additional concepts that could address other critical areas of the market:
[PLACEHOLDER - MARKET SWOT PRIORITY URL]
1. **Prime (AI-Augmented Security Integration in CI/CD):** Augments DevSecOps Engineers by automatically scanning code for vulnerabilities, testing changes, and providing real-time security feedback directly within the CI/CD pipeline.
2. **Liaison (AI-Powered Customer Engagement):** Augments Sales and Marketing Teams by profiling leads, personalizing outreach, and predicting buying intent to shorten the long sales cycles in regulated industries.
3. **Guardian (Adaptive Runtime Protection):** Augments Security Engineers by dynamically adjusting app protection policies in real-time based on the user's context, device posture, and the current threat level, effectively implementing a Zero Trust model.
4. **Flux (Multi-Cloud Risk & Performance Optimization):** Augments Cloud Operations Teams by monitoring cloud infrastructure for risks, optimizing costs, and automating failover protocols to mitigate dependency on a single provider.
5. **Optima (Dynamic Pricing Optimization):** Augments Pricing Managers by analyzing competitive pricing and customer usage data to recommend optimal pricing tiers that maximize revenue and combat margin pressure.
6. **Echo (Intelligent Customer Education):** Augments Customer Success Teams by delivering personalized onboarding materials and interactive demos that simplify complex security concepts for non-technical buyers.
7. **Mentor (Cybersecurity Talent Augmentation):** Augments HR and Team Leads by automating routine security tasks and providing personalized learning paths to upskill junior team members, mitigating the impact of the talent shortage.
8. **Aegis (IP Protection & Monitoring):** Augments Legal and R&D Teams by automatically scanning patent landscapes to identify potential infringement risks and new IP opportunities.
9. **Insight (White Space Opportunity Identification):** Augments Strategy Teams by analyzing market data to uncover unmet needs and underserved niches, such as the security needs of small and mid-market enterprises.
10. **Shield (AI-Powered API Security & Key Management):** Augments Cloud Security Engineers by automating the entire lifecycle of API keys—issuance, rotation, and revocation—and detecting anomalous usage patterns.
### Sub-section C: The Ultimate Vision - An Interdependent AI Agent System
While individual agents are powerful, the ultimate evolution is a fully integrated **system of agents** that work in concert, orchestrated by a master agent to optimize the entire value chain.
[PLACEHOLDER - MARKET AGENT SYSTEM URL]
Imagine a system called the **Unity Command Center**, a master orchestrator that has a real-time, holistic view of the entire business. It oversees five specialized sub-agents:
- **Nexus Sentinel (DevSecOps Agent):** Manages the secure CI/CD pipeline.
- **Mesh Sentinel (API Guard Agent):** Secures all API endpoints.
- **Sentinel Watch (Threat Agent):** Scans for and responds to threats.
- **Nimbus Vault (CloudKey Agent):** Manages all encryption keys.
- **Echo Care (Client Insight Agent):** Monitors and supports all customers.
When **Nexus Sentinel** detects a new app version ready for deployment, it signals the **Unity Command Center**. The Command Center instructs **Mesh Sentinel** to provision the necessary API policies and **Nimbus Vault** to generate the required cloud keys. As the app is deployed, **Sentinel Watch** begins active monitoring. If a customer reports an issue, **Echo Care** analyzes it and might find it's a known bug. It feeds this information back to the Command Center, which can then instruct **Nexus Sentinel** to prioritize a fix in the next sprint.
This is a vision of a business operating with unparalleled efficiency, agility, and intelligence—a truly AI-augmented enterprise where human talent is freed to focus on strategy, innovation, and high-value customer relationships, while the complex, data-intensive operations are managed by a coordinated team of dedicated AI agents.
\*\*\*
## **Conclusion & Strategic Exchange**
Our deep dive into the Mobile App Security SaaS B2B market reveals a sector at a critical inflection point. This is a **€3.6 billion** ecosystem, not just defined by its impressive **17% annual growth**, but by the profound technological and regulatory forces reshaping its future. The market is segmenting into distinct, high-value verticals—Fintech, Healthcare, and a digitalizing Retail/Mobility sector—each demanding a uniquely tailored Go-To-Market strategy. Success is no longer a matter of having a good product; it is a matter of achieving deep vertical fluency and solving specific, high-stakes problems like compliance automation and fraud prevention.
The competitive landscape is a dynamic arena where technological innovation is the primary axis of differentiation. Power is consolidating around players who can master the dual challenge of pioneering advanced, AI-driven runtime protection while also delivering seamless, enterprise-grade integration into complex CI/CD pipelines. An analysis of the market's SWOT profile underscores this: the key opportunity lies in leveraging AI to amplify strengths in innovation and mitigate weaknesses in integration complexity and long sales cycles.
This analysis brings us to a clear conclusion: the future of this market belongs to the AI-augmented enterprise. The strategic deployment of specialized AI agents—whether for predictive threat detection, automated compliance, or intelligent customer engagement—is moving from a conceptual advantage to an operational necessity. These systems represent the most potent lever for building a durable competitive moat, delivering unmatched value to customers in regulated industries, and capturing the lion's share of this rapidly expanding market. The decisive factor for leadership will be the ability to integrate AI not just as a feature, but as the core operating system of the entire value-creation process.
If you are interested in this topic you can follow these next steps:
1️⃣Download below the full Mobile app security SaaS B2B market study in pdf format
2️⃣ Get additional insights of this market by reading our memo of an interesting company in this market called Approov Mobile Security (Secure mobile apps & APIs against evolving threats)
3️⃣ If you want us to build a custom AI system and dedicated AI agents, book a strategic discussion with an AI Partner : https://forms.proplace.co/meet
.png)